When you deploy your first workload in AWS, one of the first things you’ll encounter is Amazon VPC (Virtual Private Cloud) , the invisible network layer that usually is the fundamental building block of the AWS ecosystem.
This article breaks down what a VPC really is, how it works, and how it maps to the concepts you already know like routers, firewalls, subnets, VRF’s, routing and all.
Fundamentals of VPC
Think of a VPC as your own private data center inside AWS, one that’s software-defined, highly scalable, and globally available.
Initially when you create a new AWS account, now a default VPC will automatically be assigned to your new account, however you can create your own VPC as per your custom setup.
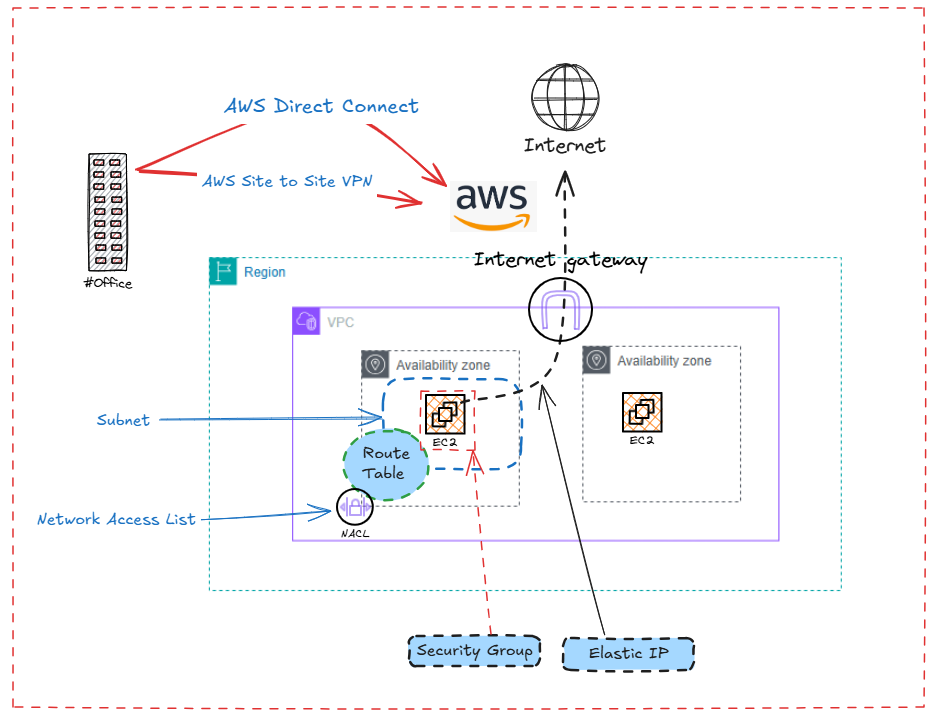
When you create a VPC, AWS allocates a private IP space (using RFC 1918 ranges like 10.0.0.0/16) within a selected AWS Region. Inside that virtual network, you control:
- Subnets – Logical divisions of your network mapped to specific Availability Zones. Each subnet will be associated with a routing table and Network Access Control Lists NACL, can be used to secure access on the subnet level.
- Routing Table – How packets move between subnets, to the Internet, or to on-premises sites. This is
- Security Group – Inbound and outbound filtering applied to Instances, it’s like a firewall, stateful, they track TCP, UDP, and ICMP connection.
- Connectivity – Integration with VPNs, Direct Connect, and VPC Peering for hybrid environments
- Network ACL : are stateless and by default allow all packets, and can be used to deny and permit specific CIDR ranges.
- Elastic network Interface (ENI): its like a Virtual Network interface Card and can be moved around to different instances.
- Elastic IP Address: It’s a static public IP that can be assigned to an ENI.
- Public IP address: publicly routable address that is reachable from the internet
- Private IP address: subnets which has no connectivity to internet
Notes About VPC:
- No Layer 2 in VPC
- Subnets are local to AZ
- Data Transfer Fee applies between AZ
- Inbound Traffic from internet is free
- Outbound traffic has a data transfer fee
- VPN connections to VPC has hourly rate charges
- Below elements are seen to be free(however always verify via latest AWS documentation to get the latest up to date pricing information:
- VPCs
- Security Groups
- Route Tables
- Internet Gateway
- Virtual Private Gateway
- Network ACL
- ENI
In short, a VPC is your slice of the AWS global network fabric, isolated from other customers yet capable of securely connecting anywhere you choose.
Mapping Cloud Networking to On-Prem Concepts
If you’re from a traditional networking background, here’s how AWS VPC concepts align with real-world constructs:
| AWS Concept | Traditional Equivalent | Description |
| VPC | Data Center or VRF | Logical, isolated network domain |
| Subnet | Logical Division of IP Network, Router port for example with an IP prefix attached. | Layer-3 segment within a VPC tied to one Availability Zone |
| Route Table | Routing Table or Policy-Based Routing | Determines next hop for traffic leaving the subnet |
| Internet Gateway (IGW) | Edge Router / NAT | Enables Internet access for public subnets |
| NAT Gateway | PAT Device / Outbound Proxy | Allows private subnets to reach the Internet securely |
| Security Group | Stateful Firewall Ruleset | Filters inbound/outbound traffic per instance |
| Network ACL | Stateless Access List | Controls subnet-level traffic |
| Elastic Network Interface (ENI) | Network Interface Card (NIC) | Connects an EC2 instance to a subnet |
| Elastic IP | Static Public IP | Persistent, portable public IP address |
Once you understand these mappings, AWS networking starts to feel less abstract and more like a next-generation version of the familiar, just without the cables, racks, or patch panels.
The Building Blocks of a VPC
1. Subnets
Each subnet lives in one Availability Zone. Think of it as your Layer-3 segment inside a fault-isolated data center.
You can create both public and private subnets:
- Public subnets route 0.0.0.0/0 to an Internet Gateway.
- Private subnets route outbound traffic via a NAT Gateway or to your on-premises network.
- Note: NAT gateway allows instances to reach the internet , but does not allow inbound traffic from the internet .
2. Route Tables
Every subnet uses a route table that dictates where packets go. AWS automatically injects a local route for intra-VPC communication and all subnets inside a VPC can talk to each other unless restricted by security layers.
3. Security Groups & NACLs
These define the perimeter and flow of your traffic:
- Security Groups act as stateful firewalls attached to instances.
- Network ACLs operate at the subnet level and are stateless (rules evaluated for every packet).
Together, they give you fine-grained control over inbound/outbound communication.
4. Internet & NAT Gateways
Gateways act as your connection points:
- An Internet Gateway connects your VPC to the Internet.
- A NAT Gateway allows private instances to reach the Internet (for updates or external APIs) without being publicly reachable.
5. VPC Peering, VPN & Direct Connect
These enable your VPC to reach other networks:
- VPC Peering connects two VPCs directly.
- VPN Connections create encrypted tunnels to your on-premises routers.
- AWS Direct Connect offers a dedicated fiber link from your data center to AWS, providing predictable latency and bandwidth.
How Packets Actually Flow
When a packet leaves an instance in a VPC, AWS’s hypervisor-managed network fabric determines the destination instantly and there’s no ARP, no broadcast, and no spanning tree. Every IP mapping is known and maintained by AWS at the hypervisor level.
Traffic between instances in the same VPC never leaves AWS’s internal backbone. Even when you communicate across Availability Zones, the packets travel via private, high-speed links and not the public Internet.
This architecture ensures:
- Predictable latency
- Elimination of broadcast storms
- Deterministic routing
- Massive horizontal scalability
Why VPC Design Matters
A well-designed VPC is the foundation of everything you build in AWS, from EC2 workloads and databases to Kubernetes clusters and AI pipelines. Poorly planned CIDR ranges or subnets can cause headaches later, especially when scaling or integrating with multiple accounts.
When designing, always consider:
- Future expansion (leave room for growth in CIDR planning)
- Cross-account or multi-region communication
- Security segmentation and least-privilege access
Hybrid connectivity (VPN/Direct Connect readiness)
The Takeaway
Amazon VPC isn’t just a virtual LAN, it’s a programmable, scalable, and secure global networking fabric that adapts to the way modern businesses operate.
If you understand the principles of subnets, routing, and firewalls, you already have 70% of what you need. The remaining 30% is simply learning how AWS abstracts and automates those same fundamentals at planetary scale.
What’s Next
In the next article of this series, we’ll go deeper into “CIDR Planning, Subnet Isolation, and Address Design in Amazon VPC” where we’ll walk through real-world design blueprints for multi-AZ deployments and hybrid network planning.